Unmatched GovCloud Security with NTS and AWS

New Tech Solutions, Inc. (NTS) is a trusted Advanced Amazon Web Services (AWS) Consulting Partner serving the Public Sector since 1997. Whether it’s protecting existing workloads or building new AWS GovCloud environments, NTS deploys robust security solutions to meet the unique demands of the US Government. This article will introduce our core AWS security principles and how we work with US Government customers to develop System Security Plan (SSP), design a Zero Trust Architecture (ZTA), and keep current with the latest AWS security services and best practices.
For NTS, security in the cloud starts on day one of any consulting project. We believe in the foundations of a strong ZTA developed from an SSP. The SSP is a comprehensive organization or program level document that identifies the security requirements of a system and the controls to meet them. Over the years NTS has adopted its own internal version of an SSP which we use as a baseline to combine and develop with our customer’s SSP depending on requirements. NTS adheres to the National Institute of Standards and Technology (NIST) standards for our SSP and guidelines for assisting customers create their own unique SSP, which include but not limited to, NITS SP 800-171 Rev. 2, 800-17 Rev. 1, 800-53 Rev. 4, and 800-207 (Zero Trust Architecture). Secondly, NTS follows the principles of the AWS Well Architected Framework for Security, Reliability, Cost, Performance, and Operational Excellence when developing security controls in AWS. Another key factor for US Government customers is understanding the line of responsibility in the AWS Shared Responsibility model. NTS clearly defines the security “in” the cloud and security “of” the cloud allowing for accurate and effective system security policies. Overlap in shared controls between AWS and the customer do exist potentially exposing vulnerabilities but can be successfully circumvented through patch management policies, configuration management processes, and AWS training. Guided by these NIST and AWS principles an inclusive SSP is created and followed by NTS and the customer.
With a completed customer SSP, NTS goes to work on the ZTA of AWS account creation and security controls. Building on the zero-trust idea that no user, packet, or network is safe, ZTA comes into the light as the leading design principle for cloud solutions.
“Zero Trust Architecture is an end-to-end
approach to network/data security that encompasses identity credentials, access
management, operations, endpoints, hosting environments, and the
interconnecting infrastructure” – NIST 800-207
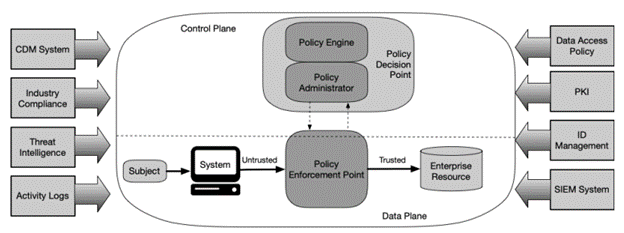
Driven by NIST standards and coupled with AWS security services and best practices, NTS can accomplish ZTA for cloud architecture re-designs and new deployments. Multi-account designs and AWS Organizations shrinks the attack surface when NTS designs ZTA. Segmenting logical functions further beyond the account boundary allows for a gateway security component in front of critical application-based segments. This gateway security component (policy enforcement point) can consist of AWS Transit Gateway, VPC, WAF, GuardDuty, and many others. Using AWS Organization’s Service Control Policies (SCP), Organizational Units (OU), and IAM US Government customers have a control plane and policy decision point. These AWS components are the foundation of ZTA and allow for the application-based segments (enterprise resources) to have trusted access.
In addition to ZTA principles and SSP
control mapping, NTS monitors new AWS services released to GovCloud on a weekly
basis so we can continuously keep our customers up to date with the latest
security offerings from AWS. NTS’ dedicated and skilled AWS Engineers can
quickly learn the new service and recommend implementations to our various
customers through already established (or new) Professional Services or Managed
Services. As a recent example, earlier this year was the release of Amazon Detective to AWS GovCloud Regions
(US-West and US-East). Already familiar with this service being available in
the AWS Commercial Regions, our AWS Solutions Architects were able to
communicate its importance and use-cases to our Federal customers.
“Amazon Detective can analyze trillions of events from
multiple data sources such as Virtual Private Cloud (VPC) Flow Logs, AWS
CloudTrail, and Amazon GuardDuty, and automatically creates a unified,
interactive view of your resources, users, and the interactions between them
over time.” – Amazon Web Services

Once Detective has learned the AWS account(s) behavior, for a one-month period, baselines of user, API calls, and other AWS Services activity can be established. Now, Detective can spot abnormalities across these three vectors and provide helpful visualizations of resources historical data or potential threat activities. Integrating Detective with AWS GuardDuty allows the NTS SOC to get real-time views of potential threats and quickly analyze them to determine if a finding is valid and its impact level. Investigating GuardDuty findings with Detective pulls logging information from AWS CloudTrail and VPC Flow Logs to visualize affected resources, originating IP and trends, target resource ID and IP, and the
account in question. All these entities related to the single GuardDuty finding reduces the time it takes to spot, investigate, and archive false positive findings. In the event the finding is a threat and Incident Response (IR) processes are activated, NTS can quickly assess the finding to determine threat activity, followed by isolating the resource, and hunt down the threat as needed until the incident is resolved.
NTS is devoted to keeping our US Government customers AWS workloads secure through our experience with the best practices discussed in this article. Find out how NTS can enhance your AWS security posture today.